Protect Your Data from Yourself – SAP UI Masking and Logging
Today’s businesses have a legal requirement to protect the personal information of individuals, including their employees, customers, and suppliers. Regulations like GDPR, HIPAA, the Sarbanes–Oxley Act, and other agreements show the growing concerns and possible repercussions for neglecting data protection practices. A HIPPA violation can cost up to $50,000, and a GDPR fine could cost 4% of a company’s global revenue. While there are many ways to increase data security, one way a company can start is by helping their employees avoid inadvertent data breaches.
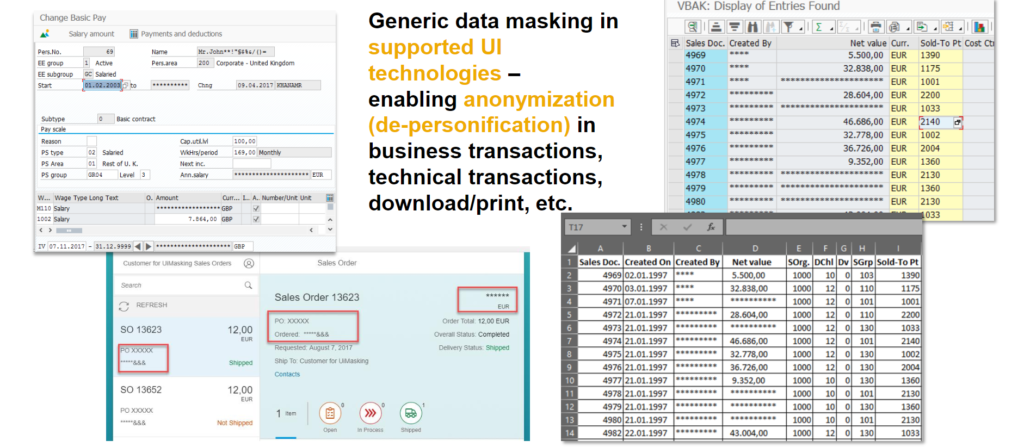
Tracking who has access to sensitive information usually requires a step beyond a basic system setup. SAP provides two products to help business understand who is viewing what. SAP UI Masking conceals specific data, such as values in fields and columns, unless that information is required for a task. SAP UI Logging allows for more accessibility while logging and analyzing user access. This feature is useful for post-breach audits.
While SAP UI Masking is not a new tool, recent updates allow for specific fields to be disabled from editing or hidden. The “reveal on demand” feature prompts a user to enter the specific reason they need access to view or edit data. Applying logic to the masking functions can block users from viewing certain financial information or from data outside their relevant regions. UI Masking is performed in browsers like SE16 before other users can view the data.
Using SAP UI Masking and Logging in Your Business
Masking examples for proactive data security
- Hiding a customer’s address or SSN from a sales rep until that information is necessary
- Salespeople could see all records, but only be able to edit their own data
Logging examples for data breach audits
- A nurse could have full access to any data they need while caring for patients, while the content they accessed is recorded for security purposes
- Reviewing an administrator access
Key Functionality – Field Masking in SAP Screens
© SAP SE or an SAP affiliate company. All rights reserved.
Increasing expectations for data security requires businesses to be proactive in their security measures. How is your business addressing heightened expectations around data and information security? To learn more about how Clarkston can help your company fight next-generation threats to privacy and security, subscribe to our insights below or contact us today.
Subscribe to Clarkston's Insights
Coauthor and contributions by Steve Barrett



